
Would you believe that 90% of all cyberattacks start with an email? You probably know about email scams and phishing attacks, but have you heard about email spoofing? Today, every kid has a go-to email spoofing website for free pranks aimed at their friends, but email spoofing is not a joke. It’s way more serious than that.
In this article, we’re exploring the real-life examples and dangers of email spoofing and how to spot a spoofed email and stay protected against this online threat.
In this article
What Is Email Spoofing?
We can tell you right away – a spoofed email is not the same as a virtual mail ID. It’s more like a fake SMS, only sent over the internet. So what is email spoofing, exactly?
It’s confusing because, in specific scenarios, spoofing is a positive thing.
For example, VPNs and proxy servers rely on location spoofing to obtain anonymity for their users. In this context, spoofing can help circumvent frustrating (usually illegal) online restrictions and give you access to geo-blocked movies, censured news, or discount prices.
Spoofing means concealing one’s identity – either for good or for evil.
Now that you know this, can you take a guess on what email spoofing is?
Email spoofing is a tactic often used by cybercriminals. With it, malicious actors on the internet mask their identity, but not only that. They also pretend to be someone they are not in order to trick you into giving them confidential information, such as a password or PIN.
If you’ve ever received an email from a colleague or your favorite brand where something felt off – for example, the sender asked a question they already knew or would never ask – that’s a textbook example of email spoofing. Hopefully, you didn’t already fall for it.
How Email Spoofing Works

The main goal of email spoofing is to gain and misuse your trust.
Unfortunately, that’s not all. Once the sender tricks you into believing that you’ve received an email from someone you know or who is trustworthy, they usually ask for confidential information, steal your credentials (and money), or infect your PC with malware.
Essentially, email spoofing is an exploitation scam, but it’s not only for the naive. These emails range from obviously fake to difficult to identify and come in several types:
- Legitimate domain spoofing – Legitimate domain spoofing is probably the most difficult type of email spoofing to identify, which makes it the most dangerous. It can trick even the most scam-aware and vigilant internet users so nobody’s safe.
- How does it work? Well, the clue is in the name. It’s called a legitimate domain because its display name and the sender’s address appear 100% legitimate. Criminals create this illusion by manually changing the “From” and “Reply To” fields.
- Look-alike domain spoofing – A little easier to spot, as long as you’re careful and you know what to look for, is look-alike domain spoofing. These emails look like they were sent by famous and generally trustworthy organizations, businesses, and brands.
- However, if you look closely, the scam is evident. In most cases, there’s a typo in the domain name, such as “gooogle.com” instead of “google.com.” This type of email spoofing plays visual tricks on unsuspecting victims by hiding in plain sight.
- Email display name spoofing – The third most common type of email spoofing should be the easiest to notice, but it still tricks hundreds of innocent targets every day. How? By taking advantage of the fact that we often check our emails in a hurry.
- When we do so, we can easily fail to notice that the display name doesn’t match the sender’s address. The email might look like it was sent to you by Nicole from accounting, but in reality, it was only made to look that way. Don’t fall into this trap.
Differences Between Virtual Mail IDs and Fake Emails

Many targets of email spoofing never realize they’ve been duped. This type of online scam is difficult to eradicate because scammers keep getting better at faking emails.
Virtual mail IDs only complicate things further. Often used by businesses and organizations to create a professional image, they conceal the real domain name and the email address of the sender. So instead of name@gmail.com, you will see name@businessdomain.com.
Aside from professional appearance and branding, there are many other reasons for using a virtual mail ID. Most notably, you don’t ever have to change your virtual address.
Regardless of your current domain name and no matter how often you switch between them, your virtual mail will keep forwarding all your emails to your actual email address.
But unlike virtual mail, fake emails are often sent from public domains and include spelling mistakes. Even beyond this, there’s always a way to spot a fake email by looking at its content and analyzing its intent. A fake email will always prompt an action, like following a shady link.
Attackers Can Make Fake SMS Messages as Well
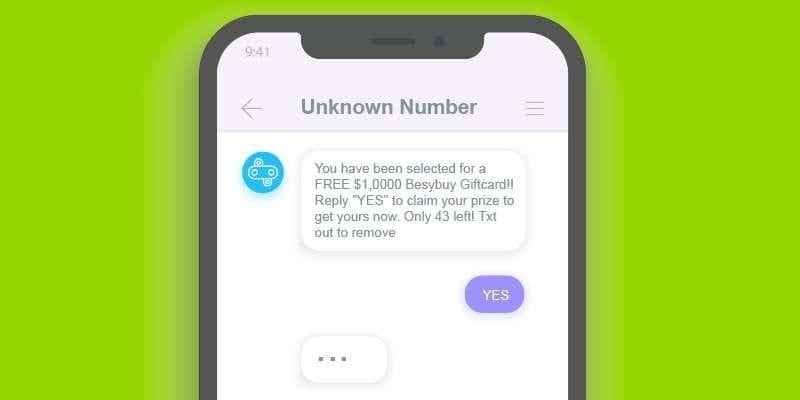
Emails are not the only type of message-based threat. There is also SMS.
When you search for “fake SMS messages” online, you get more results for how to create and send them than for how to identify them. This is pretty alarming, to say the least.
You should never respond to a fake SMS, but how do you identify it as fake?
There are a couple of red flags to watch for. Like with email spoofing, a fake SMS will try to trick you into doing something. There will usually be a link you will be asked to follow – to collect a prize you’ve randomly won or to download something you need for free, for example.
In addition to this, the sender’s number will be unusually long, as if the SMS was coming from a foreign country. There are often spelling mistakes or poor grammar in it, too.
What else to watch for? A fake SMS might contain a verification code that you didn’t ask for or ask you to verify one of your accounts. This is extremely dangerous. Worst case scenario, you can be scammed into giving criminals access to your online wallet – and your money.
Dangers of Email Spoofing

You don’t need to be in cybersecurity to understand that email spoofing is dangerous. But what you might not realize is that this tactic goes beyond personal attacks on somebody’s banking account or PC. Depending on the scale, spoofing can take down entire organizations.
Let’s say you receive one of these emails while at work. Even if it arrives in your personal mailbox, scammers can use it to access your business network and spread malware.
From there, they can inflict substantial damage on your organization. The number of threats that could be carried out this way is a scary one – ranging from relatively harmless phishing to MITM attacks. In any form or size, a data breach is usually disastrous for a business.
In almost every case, whether the target is an individual or a business, scammers use email spoofing to obtain confidential information that can be used in various scenarios – they can gain a foothold inside a secured network, transfer funds, or even steal someone’s identity.
And if you think you’re not important enough to be targeted for identity theft, you’re selling yourself too short. Criminals can use your name to target somebody on your contact list or business network, probably ruining your personal and professional reputation in the process.
Learning to Spot and Avoid Spoofed Emails
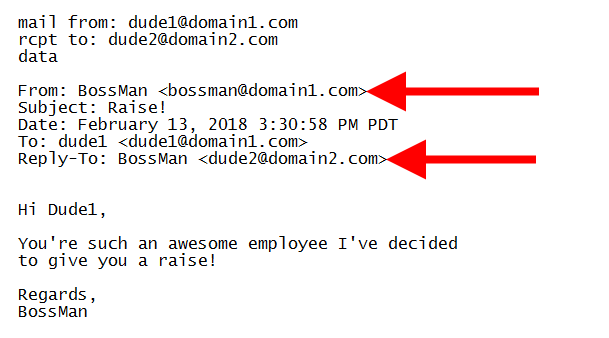
Can email spoofing be avoided? The answer is yes – up to a certain extent.
Because the internet is a network, we’re responsible not only for ourselves but for other people as well. So before anything else, it’s crucial that each one of us gets educated on the dangers of email spoofing and similar practices, as well as how to recognize and report them.
Awareness is the first line of defense against cybercrime. With that in mind, we’ve drafted a checklist of things to be aware of every time you receive a suspicious-looking email:
- If the email domain name doesn’t match the website, it’s almost certainly fake.
- If there’s a link for something you didn’t ask for, verify the email’s credibility first.
- If somebody you know is asking for an uncharacteristic favor, make a phone call.
- Does the email contain typos or grammar mistakes? That’s a huge warning sign.
- Fake emails usually prompt some kind of action and create a sense of urgency.
There are two basic rules of online security. First and foremost, avoid following out-of-place links. And second, you should never share your personal information and confidential credentials with anyone over the internet – whether or not there’s any reason for suspicion.
How to Protect Yourself for Free From Email Spoofing

While cybersecurity awareness and common sense provide a foundation for building a safer online environment for everyone, they are usually not enough to safeguard bigger teams and organizations from the many perils of cyber threats such as email spoofing.
Luckily, there are email security protocols that can help automate this. SPF, DKIM, and DMARC are widely regarded as the most effective, so they are most commonly used, too:
- SPF (Sender Policy Framework) – The easiest way to explain this protocol is as a reverse IP lookup. It’s exactly what it does – identify the sender’s IP address and check whether or not it is authorized to send emails from the given email domain name.
- DKIM (DomainKeys Identified Mail) – DKIM is an essential email safety protocol for every serious business. It encrypts both incoming and outgoing messages, thus making sure that the only emails that come through or go out are authorized and signed.
- DMARC (Domain-Based Message Authentication, Reporting, and Conformance) – DMARC is used on top of the first two protocols to track who is sending what using your domain name, as well as to quarantine and reject suspicious and unsolicited emails.
In addition, it goes without saying that you should set up strong passwords and use reliable security software for malware protection, not only in a work environment. This should keep your mailbox 99% spoof-free. As for the remaining 1%, delete it immediately.
You Deleted an Email, But It Wasn’t Spoofed?

Did you just spot a spoofed email and start to panic? That’s nothing unusual. Email spoofing targets thousands, if not millions, of recipients every day. Sooner or later, it will arrive in your mailbox as well. As said before, you should never respond to it or click on any links.
The safest thing to do is delete a spoofed email as soon as you spot it.
But what if you delete a suspicious email and then realize it wasn’t fake?
People erase emails by mistake all the time, so there is a quick solution for this. You can retrieve the lost email but need a reliable email recovery tool like Wondershare Repairit for Email. Using this tool, you can even restore Outlook emails that have been long-deleted.
Wondershare Repairit – Outlook Repair can help you repair corrupted PST/OST files and fix various Outlook malfunctions. If you’ve suffered a virus attack or your mailbox has been infected with a Trojan, it can help you with that, too. Plus, it’s very easy to use.
Wondershare Repairit for Email is available for Microsoft and MacOS.
Conclusion
Email spoofing can put your online privacy at risk and seriously damage your business. Don’t take it for granted just because it uses cheap tricks. It’s a dangerous cyber threat that can be easily avoided, but you must practice precaution and watch for the warning signs.
And if it turns out you’ve been wrong, that’s still better than being scammed. You can always restore a mistakenly deleted email using Wondershare Repairit for Email.
